Replace your obsolete VPN with a modern
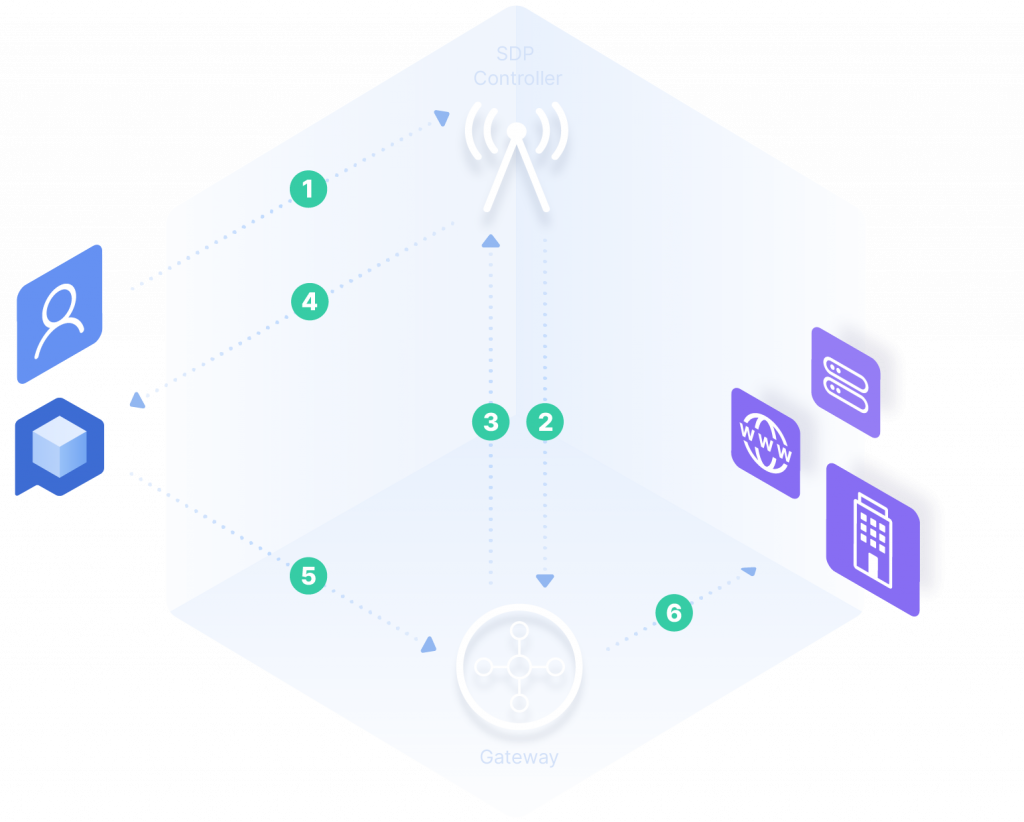
Software-Defined Perimeter (SDP)
Develop a secure, flexible access policy with a Software-Defined Perimeter (SDP). Whether your key resources are in the cloud or on local servers, SDP lets IT protect the entire network.